Vaxert
Administrator
Staff member
Owner
Super User
Descriptions
Splunk Enterprise Security is a premium security solution and enables security teams to improve security operations with faster response times, improve their security posture by getting end-to-end visibility across all machine data, investigate threats and incidents, provide optimized incident response, and conduct breach analysis, compliance, and reporting.
The Security Posture Dashboard is often the starting point, and it provides the status of your overall deployment. This fully configurable dashboard is designed to provide high-level insight into the notable events across all domains of your deployment. Splunk Enterprise Security uses correlation searches to automate detection of security violations and anomalies for security incidents. When a suspicious pattern is detected, the correlation search creates an alert called a notable event. A notable event represents one or more anomalous activities or behaviors that a correlation search has detected across potentially many data sources.
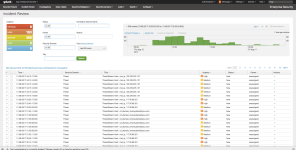
The Incident Review Dashboard is a primary interface for analysts to manage security incidents and workflows. It surfaces all notable events and categorizes them by potential severity so you can quickly triage, assign, and track issues. The Risk Analysis Dashboard displays recent changes to risk scores and objects that have the highest risk scores. As an analyst, you can use this dashboard to assess relative changes in risk scores and examine the events that contribute to an object's risk score.
The User Activity Dashboard displays panels representing common risk-generating user activities, such as suspicious website activity. This can be used for privileged user monitoring. The Access Anomalies Dashboard displays concurrent authentication attempts from different IP addresses and improbable travel anomalies using internal user credentials and location-relevant data. The UBA Anomalies Dashboard shows the anomalies identified by Splunk user behavior analytics within Splunk ES. You can use the anomalies and correlate it with any data within Splunk Enterprise Security to gain further insight into your environment's security posture.
The Asset Investigator Dashboard visually aggregates security-related events over time using category-defined swim lanes. Each swim lane represents an event category, such as authentication, malware, or notable events. The swim lane uses a heat map to display periods of high and low activity. An analyst can visually link activity across the event categories and form a complete view of a host or user's interactions in the environment.
Splunk ES includes ready-to-use dashboards that provide insight from various security domain data. The Access Domain monitors authentication attempts to network devices, endpoints, and applications within the organization. The Endpoint Domain provides insight into malware events, including viruses, worms, spyware, attack tools, adware, and PUPs, potentially unwanted programs, as well as your endpoint protection deployment.
The network protection domain provides insight into the network and network-based devices, including routers, switches, firewalls, and IDS devices. Splunk ES has a variety of advanced detection and investigative controls for investigative purposes or to detect abnormal activity that's often associated with compromised systems. This includes DNS new domain analysis, HTTP category and user agent analysis, traffic size analysis, URL length analysis, and threat intelligence artifacts.
Splunk ES includes a threat intelligence framework. By default, ES has built-in support for more than 20 threat intelligence feeds and supports ISACs, STIX, TAXII, and open source feeds. The Threat Activity Dashboard provides information on threat activity by matching threat intelligence source content to events in Splunk.
Splunk Enterprise Security help security practitioners to improve security posture, detect and investigate threats, identify, prioritize, and manage security events, make better informed decisions, and optimize incident response. Splunk Enterprise Security-- advancing analytics-driven security.
? Download here ?
Spoiler

Spoiler

Spoiler
Splunk Enterprise Security is a premium security solution and enables security teams to improve security operations with faster response times, improve their security posture by getting end-to-end visibility across all machine data, investigate threats and incidents, provide optimized incident response, and conduct breach analysis, compliance, and reporting.
The Security Posture Dashboard is often the starting point, and it provides the status of your overall deployment. This fully configurable dashboard is designed to provide high-level insight into the notable events across all domains of your deployment. Splunk Enterprise Security uses correlation searches to automate detection of security violations and anomalies for security incidents. When a suspicious pattern is detected, the correlation search creates an alert called a notable event. A notable event represents one or more anomalous activities or behaviors that a correlation search has detected across potentially many data sources.
The Incident Review Dashboard is a primary interface for analysts to manage security incidents and workflows. It surfaces all notable events and categorizes them by potential severity so you can quickly triage, assign, and track issues. The Risk Analysis Dashboard displays recent changes to risk scores and objects that have the highest risk scores. As an analyst, you can use this dashboard to assess relative changes in risk scores and examine the events that contribute to an object's risk score.
The User Activity Dashboard displays panels representing common risk-generating user activities, such as suspicious website activity. This can be used for privileged user monitoring. The Access Anomalies Dashboard displays concurrent authentication attempts from different IP addresses and improbable travel anomalies using internal user credentials and location-relevant data. The UBA Anomalies Dashboard shows the anomalies identified by Splunk user behavior analytics within Splunk ES. You can use the anomalies and correlate it with any data within Splunk Enterprise Security to gain further insight into your environment's security posture.
The Asset Investigator Dashboard visually aggregates security-related events over time using category-defined swim lanes. Each swim lane represents an event category, such as authentication, malware, or notable events. The swim lane uses a heat map to display periods of high and low activity. An analyst can visually link activity across the event categories and form a complete view of a host or user's interactions in the environment.
Splunk ES includes ready-to-use dashboards that provide insight from various security domain data. The Access Domain monitors authentication attempts to network devices, endpoints, and applications within the organization. The Endpoint Domain provides insight into malware events, including viruses, worms, spyware, attack tools, adware, and PUPs, potentially unwanted programs, as well as your endpoint protection deployment.
The network protection domain provides insight into the network and network-based devices, including routers, switches, firewalls, and IDS devices. Splunk ES has a variety of advanced detection and investigative controls for investigative purposes or to detect abnormal activity that's often associated with compromised systems. This includes DNS new domain analysis, HTTP category and user agent analysis, traffic size analysis, URL length analysis, and threat intelligence artifacts.
Splunk ES includes a threat intelligence framework. By default, ES has built-in support for more than 20 threat intelligence feeds and supports ISACs, STIX, TAXII, and open source feeds. The Threat Activity Dashboard provides information on threat activity by matching threat intelligence source content to events in Splunk.
Splunk Enterprise Security help security practitioners to improve security posture, detect and investigate threats, identify, prioritize, and manage security events, make better informed decisions, and optimize incident response. Splunk Enterprise Security-- advancing analytics-driven security.
? Download here ?
Spoiler

Spoiler

Spoiler

Last edited by a moderator: